Evolution of Internal Networking and Access

Evolution of Internal Networking and Access in Organizations
Internal networking and accessing systems for on-site traditional work environments has been very primitive with heavy reliance on a central firewall or perimeter defense boundary and all the resources grouped within it over local subnets. Accessing these would be easy using LAN connections and VPNs with certain IP restrictions and physical segmentation being used for access control.
The problem with this traditional architecture is it has its limitations with scaling and security of resources with little to no granular access control. Also, such an on-premise architecture cannot work with remote working environment. Therefore, organizations today are embracing architectures with multiple VPNs, private subnets, privileged user identities, and authentication mechanisms as a networking solution that go well with the remote work culture. These architectures promote more collaboration, streamlined deployments, and enhanced security and overall productivity, without the users being on-premises.
In this article, we will explore the evolution of internal networking and access in organizations, by examining the 4 major architectures that we see being implemented across various organizations.
Zero Architecture
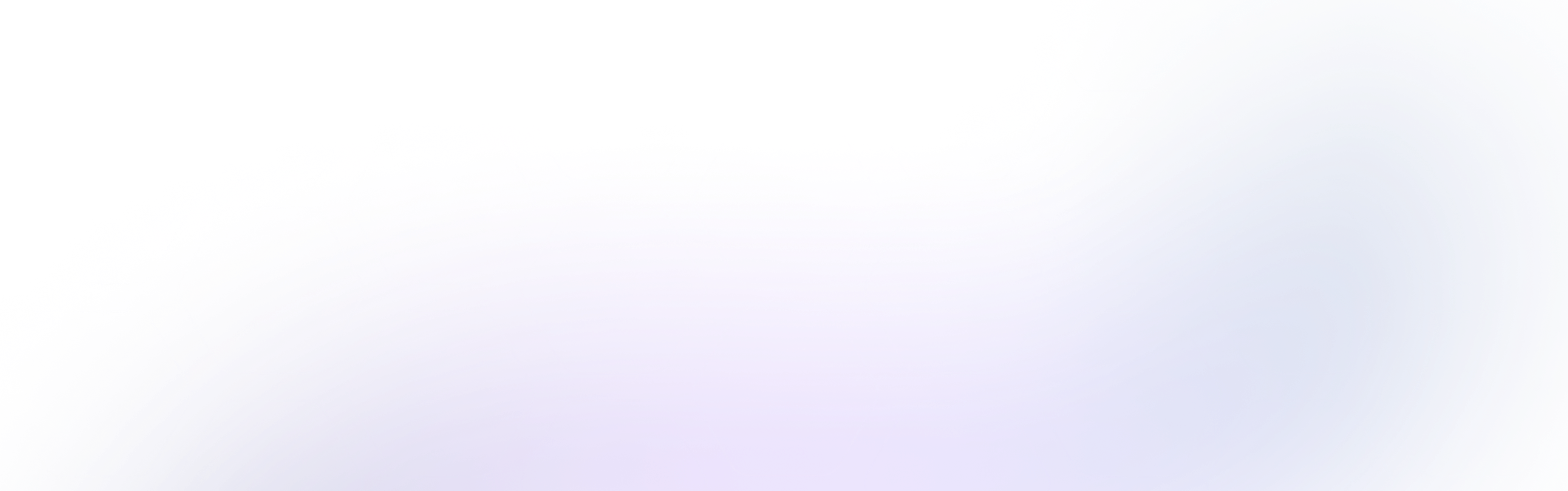
 When a startup begins building a new product, the velocity to build it and launch the best version is what is prioritized. Organizations want to keep it easy and seamless for the devs to access resources, add new versions to the code, etc., and prioritizing network and security can hinder Product-Market fit at this stage for startups.
When a startup begins building a new product, the velocity to build it and launch the best version is what is prioritized. Organizations want to keep it easy and seamless for the devs to access resources, add new versions to the code, etc., and prioritizing network and security can hinder Product-Market fit at this stage for startups.
The way most startups deal with this is as follows:
- Everything is put on the public subnet
- They use tools like Digitalocean, Railway, Heroku, render, and vercel to set up infrastructure
These platforms abstract away much of the underlying infrastructure complexity, allowing teams to focus on application development and business logic rather than server provisioning, networking, and maintenance tasks. This simplification saves time and resources, enabling developers to be more productive and deployments to be easier.
Ops are fairly easy to manage as well. All the SaaS platforms need zero configuration to work together and all this ensures a great developer experience.
While leveraging these cloud platforms can be super efficient and easy to manage, it is important to be cautious of the risks involved with having zero architecture for infrastructure, such as:
Security and Compliance
Neglecting having an infrastructure architecture can lead to security vulnerabilities and potential compliance breaches. In case a password for any resource is leaked in such a setup, the resource is completely compromised without the presence of any security infrastructure around it. Unauthorized individuals can discover organizations’ internal resources and can find try to breach these resources.
Dependency Management
Early organizations may face challenges when it comes to managing dependencies between various services or components. As the company's infrastructure scales up, it may get difficult to manage the compatibility and integration of different components. Integration of tools in such a setup can increase the surface area for external attacks as well. For E.g. when Railway is integrated with GitHub, an attempted attack on any of them becomes an attack with a bi-directional attack surface.
Port Knocking
With no architecture in place, port knocking attempts by unauthorized individuals can go undetected and it becomes difficult to respond to them. Attackers gaining unauthorized access through port knocking can compromise access to the company’s entire infrastructure and resources.
Gateway Architecture
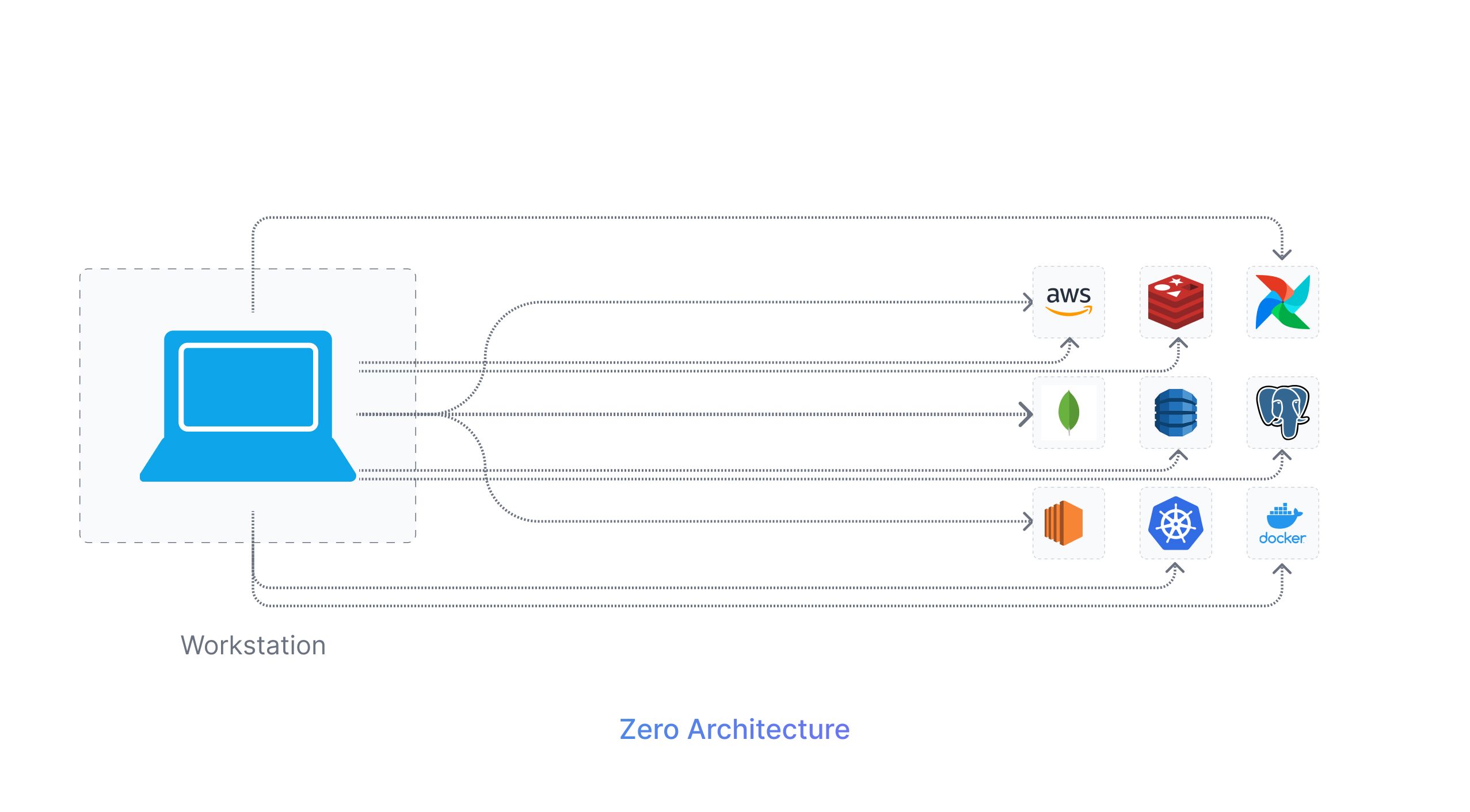
 Another commonly used architecture for infrastructure is Gateway Architecture. With the Gateway Architecture, there is a public bastion and a private subnet used for securing and managing access to resources within the organization’s network.
Another commonly used architecture for infrastructure is Gateway Architecture. With the Gateway Architecture, there is a public bastion and a private subnet used for securing and managing access to resources within the organization’s network.
The private subnet also referred to as backend subnet in this case is a portion of an organization's network that is inaccessible from the public internet. The private subnet has all the primary internal resources and services such as internal applications, servers, databases, or any other sensitive resources that need protection from direct external access. This is in contrast to the public subnet, which can be accessed directly from the internet.
The public bastion host or jump server acts as the only point of entry to the private resources and is available in a publicly accessible subnet. Authorized users connect to the bastion host using SSH and then create another proxy connection to reach the private subnet resources.
With such Gateway architecture, there is some level of resource protection due to an additional layer of security before reaching the private subnet.
While using a Gateway architecture can provide better security and access control as compared to having Zero Architecture, there are a few limitations and challenges that the devs can face with this architecture, such as:
Inferior Dev Experience
Gateway architecture provides an additional layer of security with an additional layer of complexity as well. Accessing the private subnet through the Bastion host makes the redundant step of logging into the Bastion server a daily chore for developers. Devs need to log into the Bastion every time to perform development iterations and debugging as well which introduces additional friction.
Single Point of Failure
As the bastion host is the only entry point to the private subnet, a bastion host's downtime or unavailability can lead to a major loss of time and productivity. The resources in the private subnet get cut off for use completely which is very risky.
Credential Leakage
The Bastion needs the SSH keys or username-password to let users access the private subnet. A compromise or leak of these credentials due to improper credential management can very likely lead to unauthorized access to private resources and hence is risky.
Lockdown Architecture
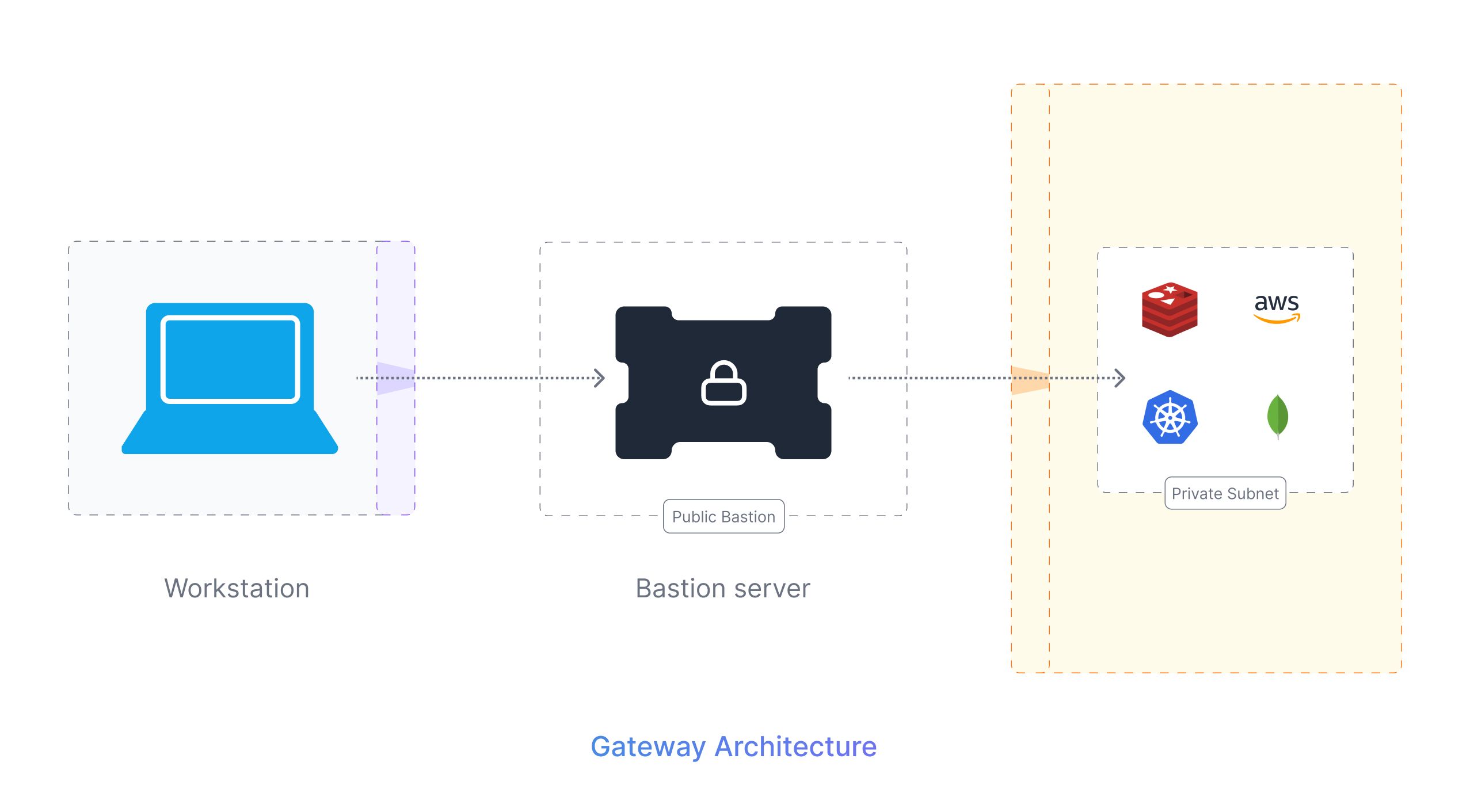
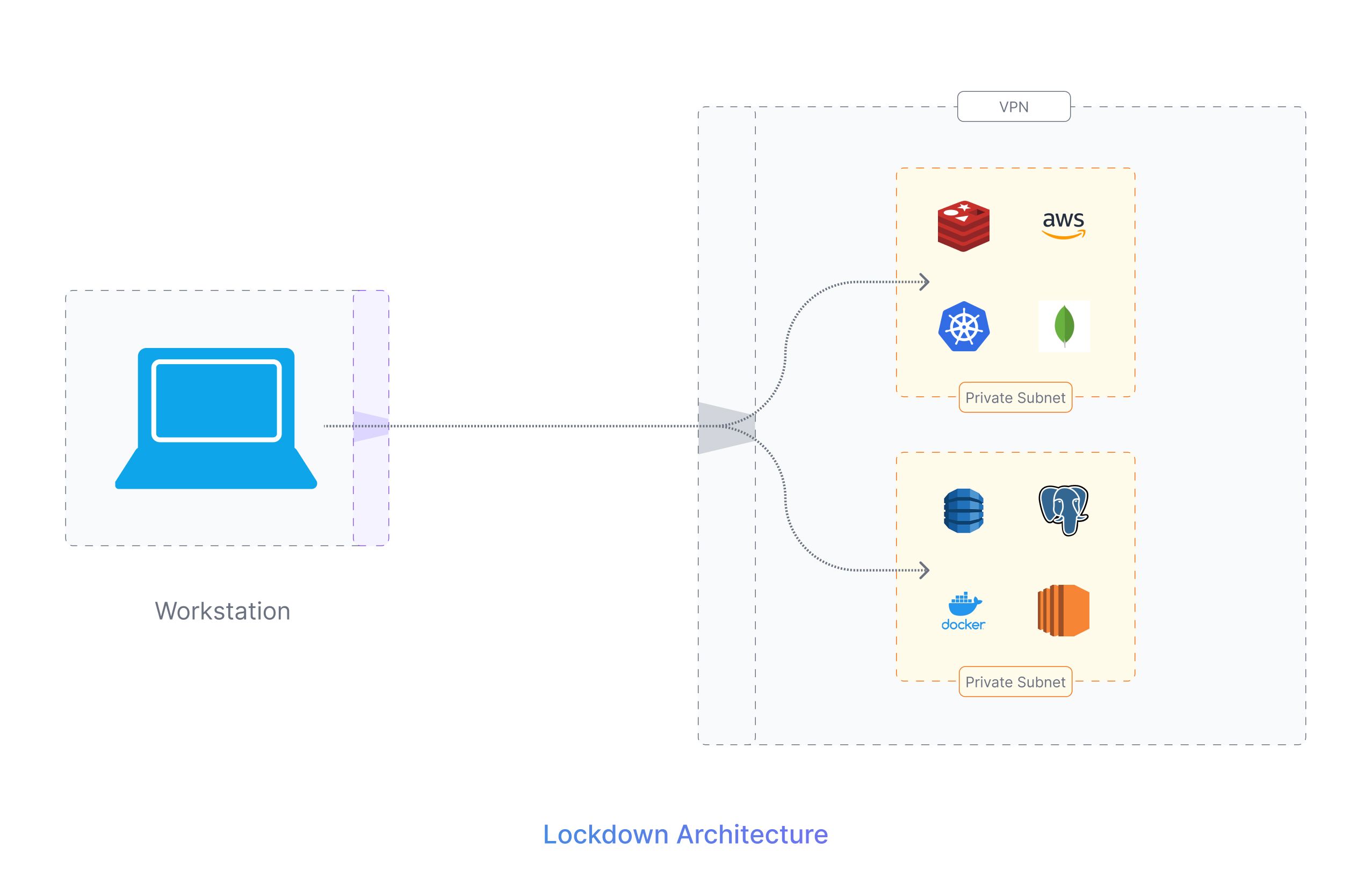 Lockdown Architecture is the next type of infrastructure architecture that improves security, provides better access controls, and minimizes exposure to public access. A Lockdown architecture has all the resources placed in private subnets and they are guarded and accessible only through a VPN.
Lockdown Architecture is the next type of infrastructure architecture that improves security, provides better access controls, and minimizes exposure to public access. A Lockdown architecture has all the resources placed in private subnets and they are guarded and accessible only through a VPN.
A VPN, or Virtual Private Network, is a secure connection between an individual device and a private network, such as the organization's internal network. VPNs are used to provide secure remote access to internal resources for employees who are working remotely or traveling. When a user connects to a VPN, they are able to access resources on the internal network as if they were physically present in the office. This ensures that sensitive data and resources are protected even when employees are outside the office. VPNs may also be used to securely connect different offices or locations of a company over the Internet.
In a Lockdown architecture, all the resources are placed within a private subnet and the VPN in such cases acts as a secure entry point to this private subnet. This setup avoids private resources from any direct external access and limits its visibility on the internet.
Though such a Lockdown infrastructure architecture enhances security and can also provide better access controls, there are a few risks with this as well.
Dependency on VPN
The setup relies heavily on VPNs adding to the organization’s infrastructure complexity and increasing the costs of maintenance and operating the complex infrastructure. Modern organizations are increasingly moving towards remote-first, cloud-based infrastructure and adopting various VPN alternatives to reduce their heavy reliance on VPNs.
Performance and Latency
Remote workers can experience performance issues with VPN services and even network latency with the performance of some applications. Also, the number of remote connections that the VPN can handle is limited and can degrade the performance and efficiency of devs.
Insider Threats
Lockdown architecture though designed to protect from external threats, still needs to address the potential Insider Threats. One single compromised user in the organization can access everything via the VPN and all the resources are exposed to such a breach. Organizations need to implement robust Identity and Access Management practices, regularly review logs, and update access permissions to mitigate insider threats.
Mission Critical Architecture
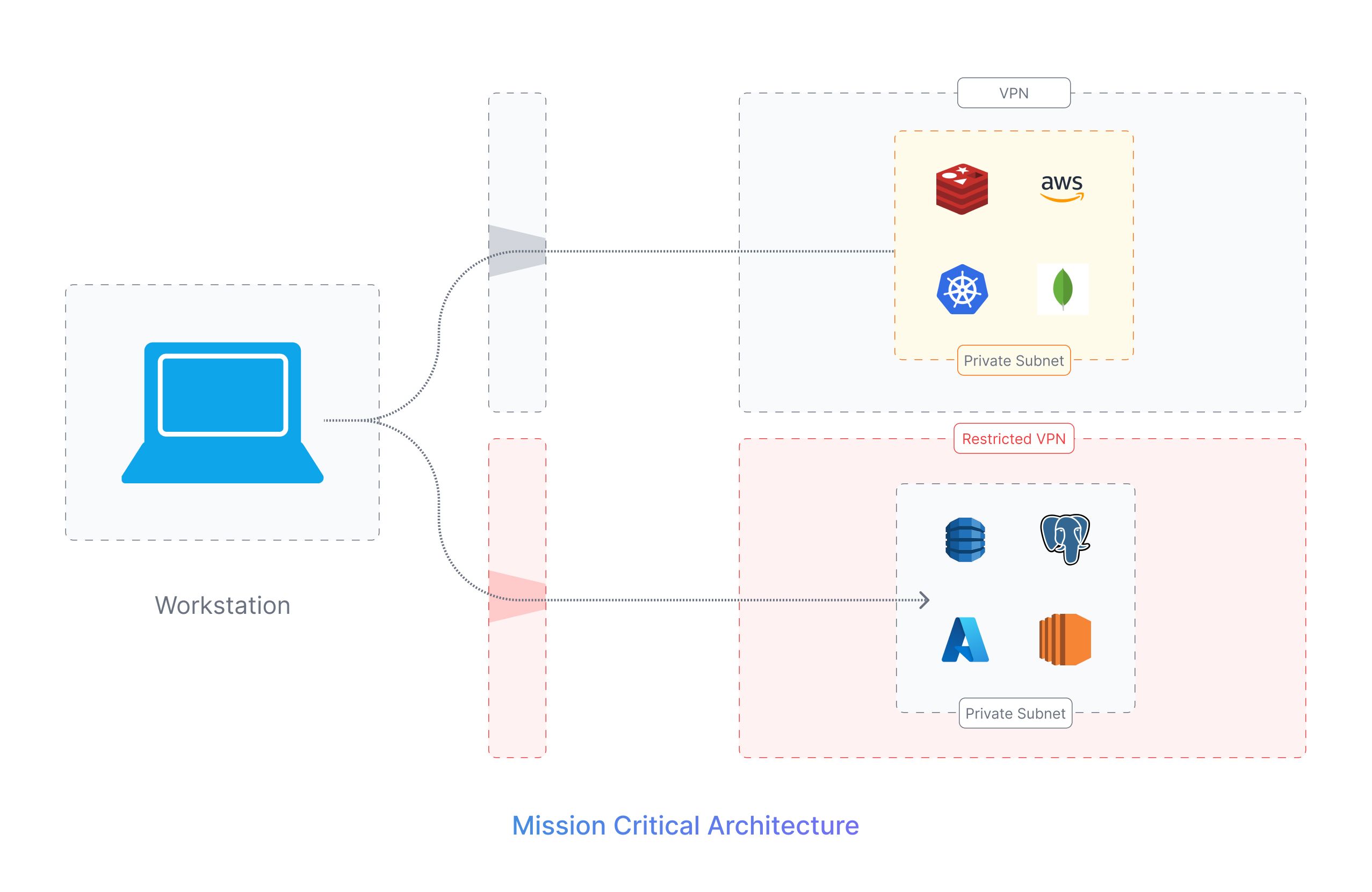 The most stringent and secure form of networking architecture can be the Mission Critical architecture where all critical as well as non-critical resources are placed in a private subnet and differentiated access control is implemented based on the level of importance of the resources.
The most stringent and secure form of networking architecture can be the Mission Critical architecture where all critical as well as non-critical resources are placed in a private subnet and differentiated access control is implemented based on the level of importance of the resources.
In such an architecture, all the non-critical resources, such as test environments, development servers, or other less sensitive resources are allowed to be accessed through a VPN. Users can connect to these resources using a VPN connection, allowing all authorized users to access these non-critical resources securely. All the important resources however such as the production servers, databases, etc. are not directly accessible to users via the normal VPN. Such resources are either completely non-accessible externally or have a different VPN infrastructure with more stringent access controls in place to access them.
This architecture allows a broader set of users to access non-critical resources via the VPN and the critical resources to be completely isolated or accessible by only a few privileged users. The architecture’s access pattern is based on the Principle of Least Privilege as well as Zero Trust Architecture as outlined by the NIST 800-207.
The only limitation of such an architecture is the complexity of this network architecture. Maintaining an infrastructure with multiple VPNs, large private subnets, and stringent access controls is a very complex task. This structure needs a well-laid plan to implement, execute and maintain to avoid this being too complex for the end users.
Simplifying Access and Internal Networking with Adaptive
While each network architecture described has its own benefits with providing security and control over access to resources, the major limitation with each of them is the need for manual provisioning and managing of user access.
This is where Adaptive comes in. Adaptive’s access management platform helps broker Just-in-Time access to all the resources and also provides centralized control over monitoring which users have access to what resources. Adaptive secures the organization’s private resources and can be easily integrated with all the architecture types no matter how big the organization is or how complex their infrastructure is.
To know more about Adaptive, book a free demo.
 SOC2 Type II
SOC2 Type II