Credential Management explained: Best Practices

What is Credential Management?
Credential management refers to the process of creating, storing, and using digital credentials, such as passwords, user names, and security certificates, to authenticate and authorize users, devices, and/or systems.
A Credential Management System is a solution that stores all the credentials centrally and gives access to the credentials to authorized users only. In growing organizations, it improves security and eases Identity and Access Management.
The goal of credential management is to provide a secure and efficient way to manage access to protected resources while minimizing the risk of unauthorized access and data breaches. This typically involves the use of secure protocols, encryption, and multi-factor authentication to ensure the integrity and confidentiality of credentials and protected resources.
Why is Credential Management important?
It helps to protect sensitive information and resources from unauthorized access
In today’s digital age, businesses rely heavily on technology and the internet to store, process, and transmit sensitive information, such as financial data, customer information, and confidential business plans. If this information were to fall into the wrong hands, it could have serious consequences for the business and its customers.
Ensure compliance with regulations such as HIPAA, PCI-DSS, SOC2, SOX, etc
These regulations have strict requirements around access controls, passwords, and audit logging. Failure to comply with these can lead to fines and penalties, thereby negatively impacting the company’s reputation.
It helps avoid secrets sprawl
A situation where the secrets (API-tokens, certificates, credentials, etc.) end up in multiple places like plain-text, dev machines, encrypted DBs, or 3rd party services. This poses security risks in case any of the above are compromised. The secrets are hard to track, update, and/or delete from everywhere.
Types of Credentials
Credentials are a way to identify and validate a user to grant them access to websites, databases, networks, etc. Credentials are categorized primarily into two types:
1. Passwords
Passwords are a form of authentication used to verify the identity of a user or system. Used to protect sensitive information and resources, such as financial accounts, personal data, and confidential documents, from unauthorized access. Passwords are the most common type of credentials used for authentication.
2. Secrets
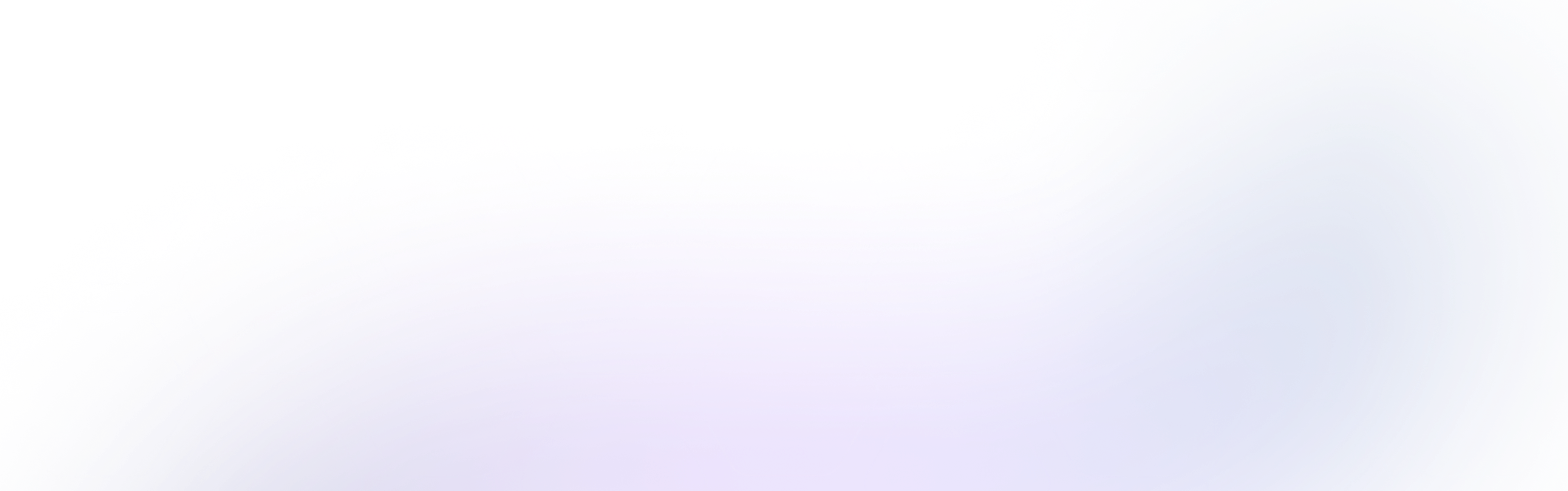
Secrets are another type of credential used for authentication, typically in the form of a token or a key. They are used to grant access to resources without the need for a user to enter a password. Examples include:
- API and other application keys/Credentials
- SSH Keys, Private certificates for secure communication, transmitting and receiving of data (TLS, SSL, etc)
- Biometric information
Password Management vs Secrets Management
People often get confused between password management and secrets management and often use them interchangeably. Let’s look at how they’re actually different.
What is the difference between Password Management and Secrets Management?
Password management and Secrets management are both practices used to secure sensitive information, but they are slightly different in their focus and use cases.
Password Management refers to the process of managing and storing authentication information, such as usernames and passwords.
The goal of Password management is to ensure that only authorized users have access to the information they need to do their jobs, while also making it easy for those users to access the information they need.
This can include practices such as password rotation, multi-factor authentication, and centralized storage of credentials.
Some of the best password managers are Google Password Manager, MacPass, LastPass, NordPass, SafeInCloud, StrongPass, EnPass, DashLane, and 1Password.
Secrets Management, on the other hand, refers to the process of managing and storing sensitive information, such as encryption keys, API keys, and other information that needs to be kept secure.
The goal of secrets management is to ensure that sensitive information is kept secure and that it is only accessible by authorized users and systems.
This can include practices such as encryption, access control, and centralized storage of secrets.
Some of the best secrets services used for secrets management are Hashicorp Vault, AKeyless, AWS Secrets Manager, GCP Key Management Service (KMS), Azure, and Doppler.
In short, Password Management deals with passwords for human authentication whereas Secrets Management deals with secrets for human-to-service or service-to-service authentication.
Both of these practices are essential for keeping an organization’s sensitive information secure, but they may be implemented using different tools and technologies depending on the specific use case.
But how about a Password Manager that can be used for both Password management as well as Secrets management? 1Password is one such example of a password management service that is working on providing both at the same time.
Can Password Management services compete with Secrets management?
A password management service typically focuses on storing, generating, and retrieving passwords for the users and can be integrated with other applications to automate the process of logging in. However, a full-featured credential management service provides more comprehensive management of authentication and authorization for a wide range of resources, including but not limited to web applications, networks, databases, and APIs.
With password management services expanding into enterprise secret management, it appears they want to handle the authentication processes of services too (like they do for humans right now) by being the proxy/interface between a secrets management service and user/services.
This requires the companies to deploy an additional service (like 1Password’s connect-server) in the K8s cluster or elsewhere, that will act as the authentication provider.
It is yet to be seen how this plays out over the years, but it definitely comes with its own benefits and shortcomings:
Benefits
- Better user experience as the password management service can handle the management and authentication of secrets for the user, simplifying the process.
- Increased security as the password management service can enforce policies and best practices for managing secrets.
- Reduced risk of human error as the password management service can automatically rotate and update secrets.
- Increased efficiency as the password management service can automate the process of granting access to secrets.
Shortcomings
- Vendor lock-in for access to Key Management Service (KMS)
- Lack of self-hosting options can be a concern for companies that want to keep their data in-house
- Leads to dependence on external services provider which results in transitive exposure to their cybersecurity weaknesses
Best practices for Credential Management
Implement an organization-wide password manager
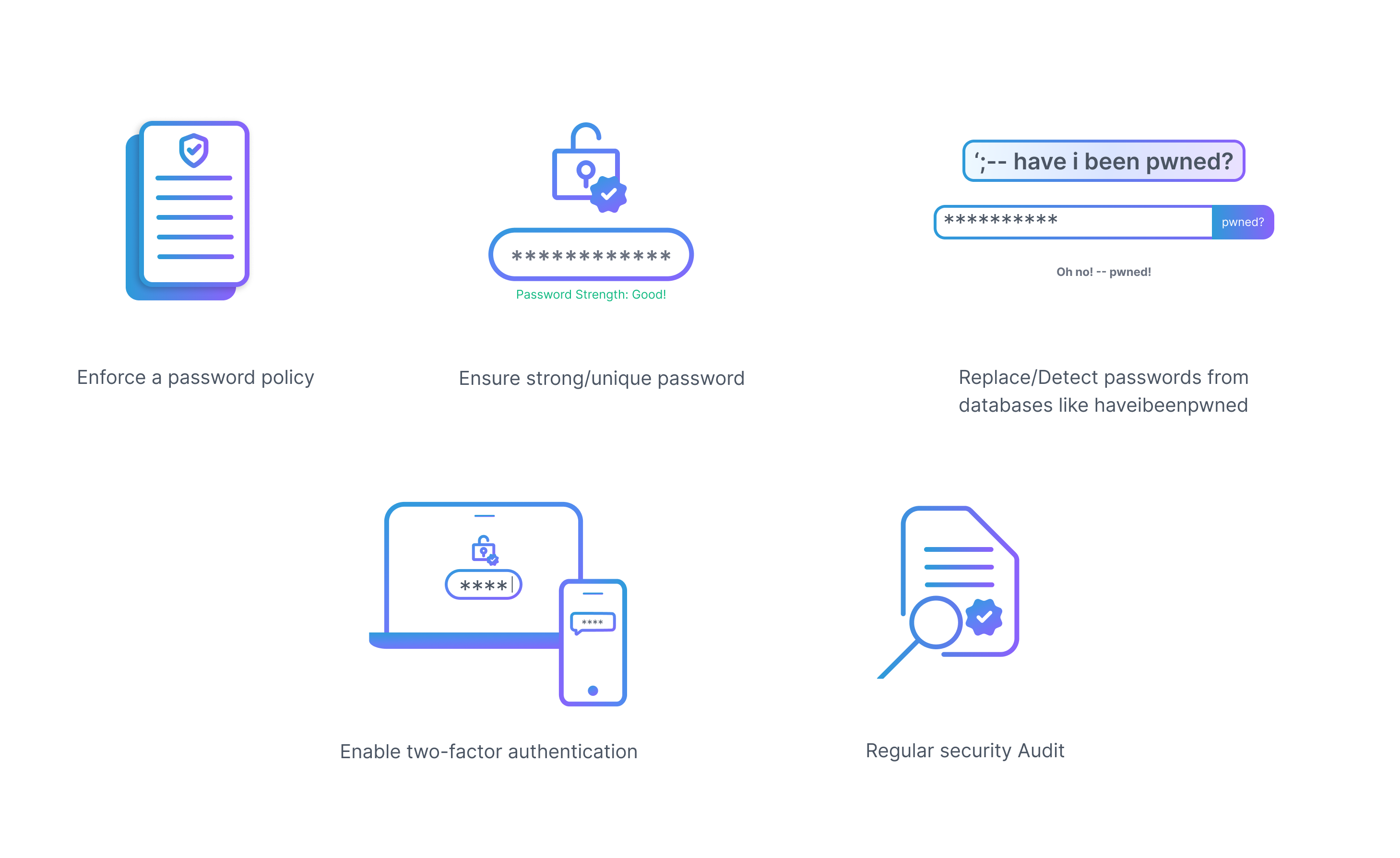
Implementing an organization-wide password manager will help to make sure every employee follows the same standards for passwords. Password managers also ensure heightened security as they store all the different passwords and avail them to the user at their fingertips. A password manager can be used to implement the following guidelines:
- Enforce a password policy
- Ensure strong/unique passwords: Strong passwords are essential for protecting against cyber attacks. It is best practice to use passwords that are at least 8 characters long and include a combination of upper and lower case letters, numbers, and special characters. It is also important to use unique passwords for each account to prevent attackers from using the same password to gain access to multiple accounts.
- Replace/detect passwords from databases like haveibeenpwned
- Enable two-factor authentication: Two-factor authentication (2FA) adds an additional layer of security to login processes by requiring users to provide a second form of authentication in addition to their password. This can include using a security token, receiving a code via text message, or using a biometric factor such as a fingerprint or facial recognition.
Remember to save backup keys to a Two-factor device, to avoid a Single Point of Failure
- Audit: A business should be able to audit and capture - activity, date, and actor for all changes taking place in the password manager.
Consolidate Identity, Access, and Authorization
Bring all aspects of user authentication, authorization, and credential-lifecycle management under one roof. This has several benefits:
- Centralized management makes it easier to monitor and control access to network resources, as all access attempts are channeled through a single point.
- Encryption at rest ensures that user credentials are protected even if the system is compromised, as the data is stored in an encrypted format that can only be decrypted with the proper keys.
- Access lists provide a more granular level of control over who has access to what resources, allowing the organization to specify exactly who can access what resources and when.
- Audit capabilities make it easier to track and investigate any suspicious activity, as all access attempts are logged and can be reviewed later.
- The ability to revoke access quickly and easily makes it easier to respond to security incidents, as access can be revoked as soon as an incident is detected.
- Unique / Dynamic tokens can be generated for each user, providing an additional layer of security as tokens can be easily invalidated if compromised.
The Future of Credential Management
The future of credentials is rapidly evolving as technology advances and cyber threats become more sophisticated. With the advent of zero trust and just-in-time access, multi-factor authentication, continuous monitoring, and granular access controls will become the norm.
Zero Trust / Just-in-Time Access
Zero Trust Network Access includes multi-factor authentication, continuous monitoring and analysis of network activity, and granular access controls based on user, device, and resource attributes. This can be achieved using technologies such as software-defined perimeter, network segmentation, and user and entity behavior analytics.
Just-in-Time access (JIT) is an approach to user authentication and authorization that grants access to network resources only when it is needed and for the minimum amount of time necessary. This approach differs from traditional credential management services, which typically grant access to resources on a long-term basis, such as through the use of static, long-lived credentials.
Credential management will still play an important role, as it is responsible for creating, storing, and using digital credentials to authenticate and authorize users and devices. However, it will be more dynamic and will be integrated with other security solutions to enable more granular and more real-time access control decisions. We will see credentials management services move away from manually created passwords to dynamic, time-gated (or privilege-gated) secrets/passwords. Adopting zero trust and JIT will complement contemporary credential management services.
Passkeys / WebAuthn
WebAuthn is a web API standard that enables web applications to authenticate users using a hardware security key, such as a USB dongle or a built-in biometric sensor on a device, instead of a password.
Passkeys are based on WebAuthn and provide password-free login to apps and websites. They are digital credentials that are kept on your devices, and biometrics are used to access them.
This improves security by making it much more difficult for attackers to steal users’ login credentials, as the hardware key provides a secure way to verify the user’s identity. Additionally, WebAuthn supports a wide range of authenticators, from those based on public key cryptography to those that use biometric data, such as fingerprints or facial recognition. Overall, WebAuthn is a secure and flexible way for web applications to authenticate users and is widely supported by modern web browsers and platforms.
More and more password management services will adopt passkeys in the future.
Time to say goodbye to VPNs
VPNs present security weaknesses by offering binary modal access to the network and its resources. They do not effectively implement policies such as least privilege, which safeguards credentials. Also, they typically lack extensive auditing capabilities beyond logging connection times and their payloads. To address these VPN shortcomings, it is time to consider adopting alternative VPN solutions.
Zero-trust gives segmented access to one or more resources as and when required. Zero-trust services have the ability to sniff traffic to resources (using special channels like bastion servers) and understand/log what changes or access is made to what resources.
Credential management services of the future, powered by Zero trust and Just in time access features, will make VPNs a thing of the past.
 SOC2 Type II
SOC2 Type II