Understanding SOC 2: Types, Principles and Benefits

What is SOC 2 compliance?
SOC 2 or formally Service Organization Control 2, is a security and privacy compliance standard that provides assurance to customers that a service provider has implemented appropriate controls to protect their data. The American Institute of CPAs (AICPA) produced SOC 2, a voluntary compliance standard for service organizations, which outlines how businesses should safeguard client data.
Each organization's specific demands are taken into account while creating a SOC 2 report. Every organization has the ability to develop controls that adhere to one or more of SOC 2 trust principles depending on its unique business practices. These internal reports offer crucial details about how they handle their data to authorities, partners in business, and suppliers.
Who needs SOC 2 Compliance?
SOC usually applies to most types of service organizations. The most common types include-
- SaaS (Software as a service) companies that offer programs, apps, and websites
- Businesses that offer management, analytics, and business intelligence services
- Organizations that manage, support, or offer advice on accounting or financial procedures
- Organizations that offer client-facing services like customer service management
- Companies that provide managed IT and security services, including those that support SOC2
You might need to comply with SOC if your business fits any of the above descriptions. While the SOC primarily focuses on these service businesses, there are other regulatory rules that AICPA offers both inside and outside of the SOC framework that extends its protections to the supply chain and beyond.
SOC Applicability to the Supply Chain
To address the demands of their own clients, service organizations collaborate with several vendors, suppliers, and other service providers. There are new dangers at every point of engagement since there are many players involved. Consequently, the AICPA has created a flexible, voluntary SOC system for the supply chain.
Companies belonging to the supply chains for service organizations may provide information about their own security procedure to them. Also, service organizations have the choice to include specific suppliers in their SOC reports. As a general rule, the more transparent a system is, the more secure it is.
The AICPA offers a wealth of useful materials to help service companies and their business partners understand the needs of all the stakeholders.
SOC 1 vs SOC 2 - What is the difference?
The main difference between SOC 1 and SOC 2 is the focus of the audit and the type of information that is covered in them.
SOC 1
The purpose of a SOC1 audit is to review and report an organization’s internal controls which focus on its customer’s financial statements. It covers controls that process and secure customer information around business and IT processes. The resulting report is used by the customer’s management and external auditors.
SOC 2
The SOC2 report is focused on an organization's controls pertaining to the 5 trust principles- security, availability, processing integrity, confidentiality, and privacy. It provides assurance that the service organization has implemented appropriate controls to meet these trust principles and protect customer data. The report is intended for use by the service organization's management and prospective customers and stakeholders.
To summarize, SOC 1 reports focus on financial controls, while SOC 2 reports focus on the 5 Trust Service Principles. It is recommended that organizations choose both types of reports if they need assurance on both financial reporting as well as information security.
There is also the third level of SOC called SOC 3. The SOC 3 reports are simplified versions of SOC 2 reports that cover many of the same principles but are intended for wide publication, such as on a company’s website. They facilitate communication of a company’s security to its stakeholders.
SOC 1 and SOC 2 produce more profound, more significant insights that companies can share with customers and stakeholders. SOC 3 reports are purely for public consumption and often cannot fulfill industry norms or requirements.
Who can perform a SOC 2 Audit?
SOC 2 Audits can be carried out by either a Certified Public Accountant (CPA) or a certified technical expert belonging to an audit firm licensed by the AICPA.
The SOC 2 Audit provides the organization’s detailed internal controls report made in compliance with the 5 trust principles. It shows how well the organization safeguards customer data and assures them that the organization provides services in a secure and reliable way. SOC 2 reports are therefore intended to be made available for the customers and other stakeholders only.
SOC 2 is different from other compliance frameworks in their audit reports, as even though the internal controls are set in accordance with the 5 Trust Services Criteria (TSC), they may vary from organization to organization. Depending on the Trust Service Criteria, an organization can have different objectives to achieve and in turn finalize different controls for their SOC 2 compliance.
It's important to note that the SOC 2 audit reports are only a point-in-time assessment and do not provide ongoing assurance to the customer. The service organization is responsible for maintaining, monitoring, and updating its controls on a regular basis to reflect any changes done to its systems and operations.
SOC 2 Trust Service Principles
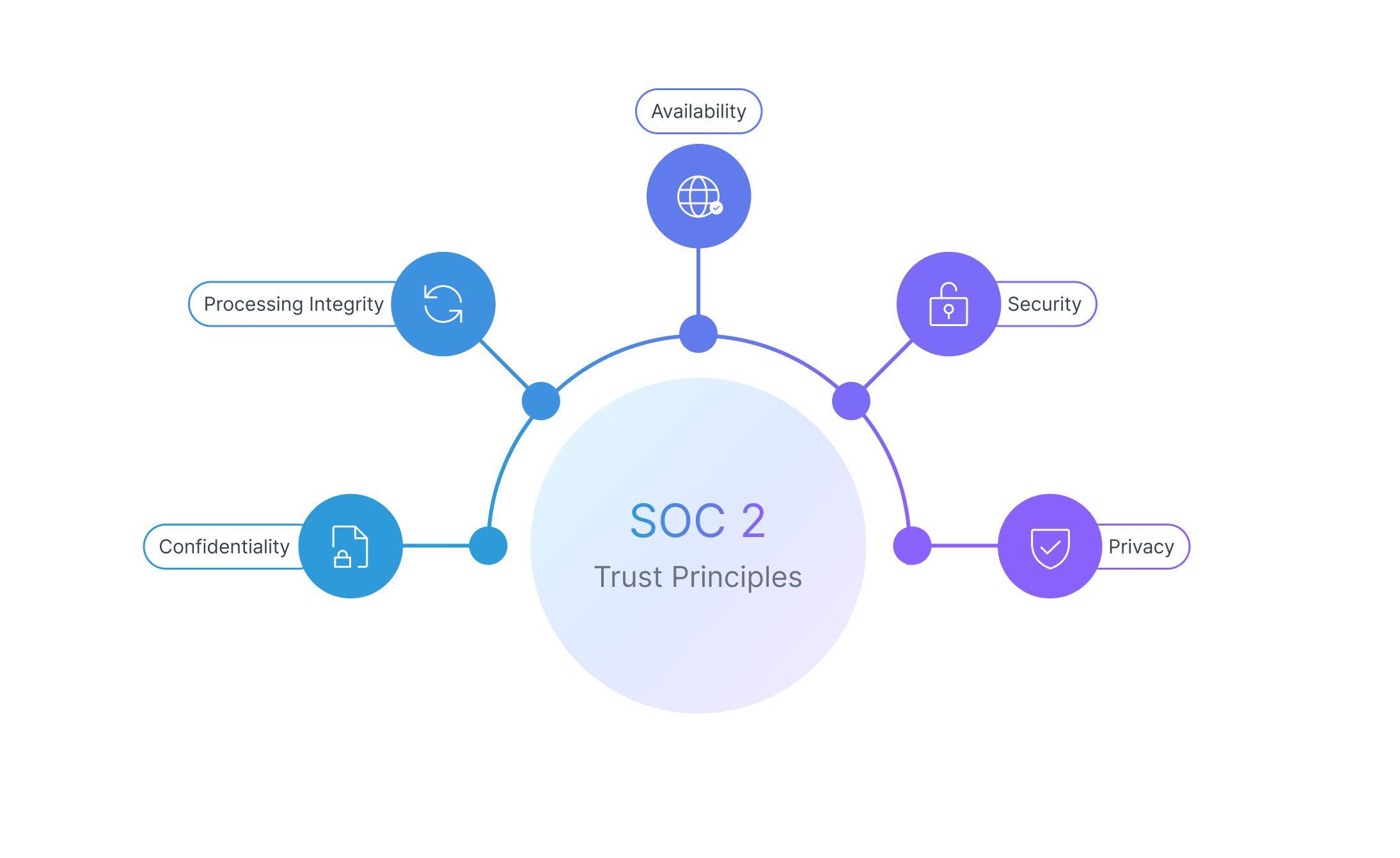
SOC 2 has five trust service principles that organizations must meet in order to achieve compliance:
1. Confidentiality
The organization must protect the confidentiality of customer data and ensure that it is only used for authorized purposes. Some of the confidentiality control checks include-
- Data classification and protection
- Data privacy and protection of sensitive information
- Encryption of data in transit and at rest
2. Processing Integrity
The organization must ensure that all transactions are processed accurately, completely, and in a timely manner. Some of the controls related to integrity include-
- Data completeness and accuracy
- System and application processing
- Data backups and recovery
3. Availability
The organization must ensure that its systems and services are available and accessible to customers as promised. A few controls that ensure the availability of data include-
- Disaster recovery plans and business continuity policies
- Monitoring and maintaining systems and applications
- Capacity planning
4. Security
The organization must have appropriate security measures in place to protect customer data which are related but not limited to-
- Physical and environmental security of facilities
- Identity and Access Management
- Network security and data protection
- Incident management and response
5. Privacy
The organization must respect the privacy rights of customers and properly handle and protect their personal identifiable information. Some of these controls might include-
- Privacy policy and data protection framework
- Data breach management and notification
Soc 2 Type 1 vs Type 2
There are two types of SOC 2 reports - SOC 2 Type 1 and SOC 2 Type 2.
SOC 2 Type 1 report evaluates if the controls are being designed and implemented successfully in the organization's systems. The goal is to check if the internal controls are sufficient to safeguard customer data. SOC 2 Type 1 audit is done at a particular point in time and hence does not offer any proof of the controls' sustained operations.
SOC 2 Type 2 report evaluates the design, implementation as well as effectiveness of the organization’s internal controls. Type 2 report tests the internal controls thoroughly over 6 to 12 months time and reports the operating effectiveness of the internal controls.
In general, SOC 2 Type 2 reports are considered to be more comprehensive and provide a more robust assessment of the service organization's controls. Overall, Type 2 audits take longer to complete and are more expensive than Type 1 audits. Customers and stakeholders who wish to understand the amount of risk associated while using the service as well as the long-term efficiency of the service organization's controls frequently choose Type 2 reports.
SOC 2 Compliance Checklist
Here is a checklist to prepare for your SOC 2 audit:
-
Type 1 or Type 2 or both: Decide whether you need Type 1 or Type 2 or Type 1 followed by Type 2
-
Trust Services Criteria: Identify which Trust Services Criteria are most valuable for your organization
-
Risk Assessment: Do an internal risk assessment to understand your current posture
-
Gap Analysis: Fill in the gaps identified during the Risk Assessment, where feasible
-
Readiness Assessment: Hire an agency or use your compliance automation tool to see your readiness for a full SOC 2 audit
Importance and Benefits of SOC 2 Compliance
SOC 2 is important for organizations as it offers great benefits which include:
1. Customer Assurance and Improved Reputation
Compliance with SOC 2 assures customers that the service organization has implemented appropriate controls to protect the data and comply with relevant regulations. This helps build trust and credibility with customers and builds the organization’s reputation in the market.
2. Overall security
The SOC 2 audit process can help organizations find and address potential security and privacy risks, which can help improve the overall security and privacy policies of the organization.
3. Compliance with regulations
SOC 2 compliance can help organizations comply with information security and privacy policies, such as the GDPR and HIPAA.
4. Informed decision-making
Organizations that use third-party service providers can use SOC 2 reports to make informed decisions about their use of services.
 SOC2 Type II
SOC2 Type II