HIPAA Compliance Checklist 2023: The 8-step Easy Guide

What is HIPAA Compliance?
Health Insurance Portability and Accountability Act or more commonly known as HIPAA is a regulatory law incorporated in 1996 by the HHS, to protect and safeguard the privacy and security of each individual's Protected Health Information.
The Office of Civil Rights (OCR) within the U.S. Department of Health and Human Services (HHS) is responsible for ensuring all the Covered Entities and their Business Associates dealing with patients’ personal and healthcare information comply with the different HIPAA rules. The OCR does investigate and impose monetary fines in case of non-compliance with these HIPAA rules by any Covered Entities or Business Associates. OCR maintains a website called the Breach Notification Portal or OCR's ‘Wall of Shame’ that posts a list of all the breaches of unsecured protected health information that are currently being investigated.
What is Protected Health Information (PHI)?
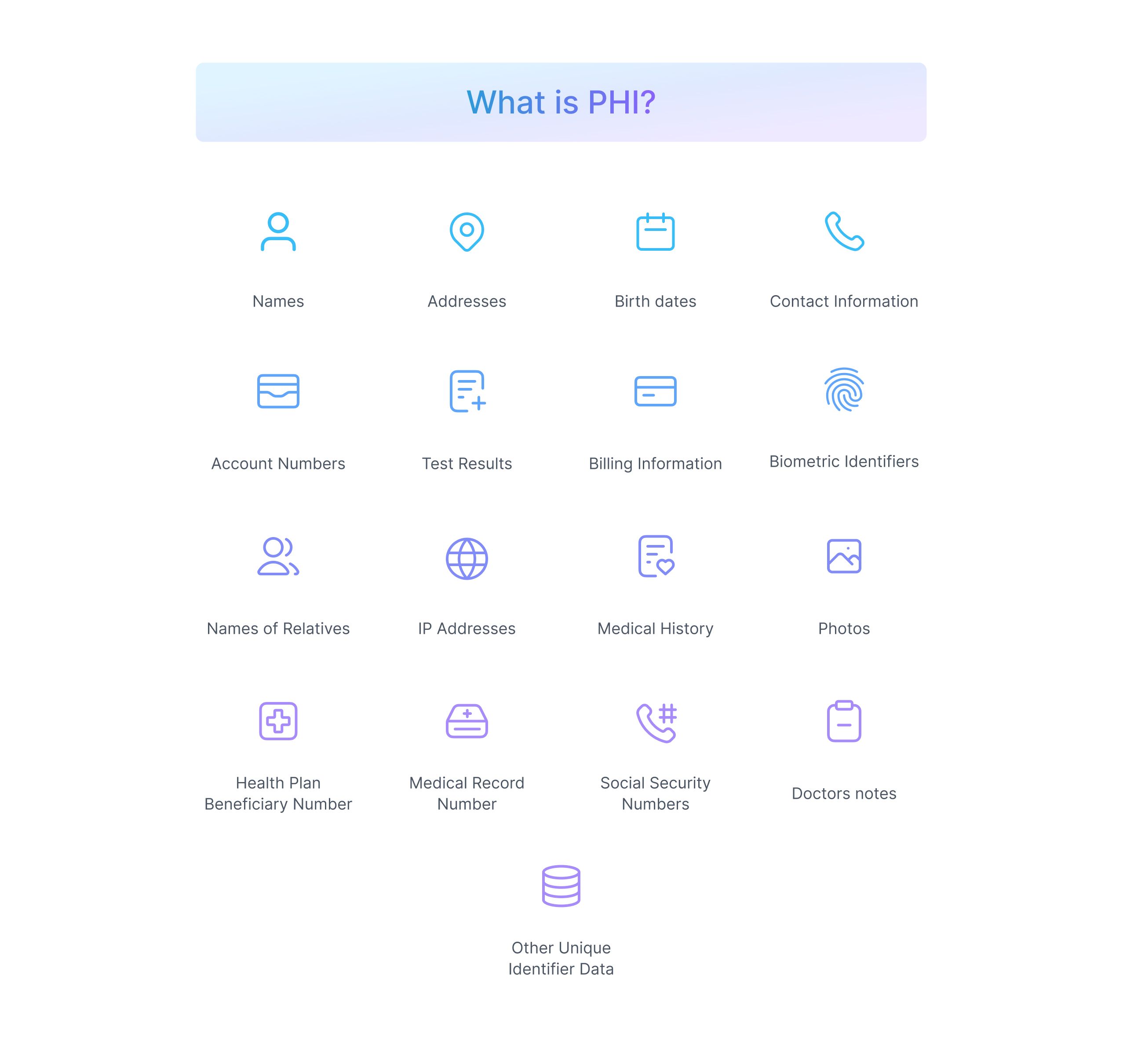
Protected Health Information or PHI is any data collected by the CE related to any individual's health or healthcare services provided that can be used to identify the individual. PHI can be data in electronic or paper-based form as well.
This includes medical records, scan reports, test results, billing information, and other personal data like contact numbers, social security numbers, addresses, and credit card details.
Why is HIPAA important for organizations?
HIPAA safeguards the PHI of individual patients. But the question at hand is why is it important to safeguard this information. And how is it important to the organizations?
The Healthcare industry is a growing target for online hacks and information breaches with this sensitive protected health information being very valuable to hackers. How valuable you may ask? Well, the average cost of a healthcare data breach is about $10 million in 2022 but, there have been much more expensive data breaches in the past that have cost as high as $400 million to the organization.
According to The HIPAA Journal, the year 2022 alone saw close to 700 healthcare data breaches that leaked 51.9 million individual records combined in the US. Hence, complying with HIPAA is needed to safeguard the protected health information of the patients and avoid leaks of their confidential PHI records.
A few other advantages of HIPAA compliance to any organization are -
- Avoiding penalties from OCR for non-HIPAA compliance
- Enhanced cybersecurity and increased protection from a data breach
- Increased patient trust in the organization
- Easier transfer of data using electronic copies of PHI
- Reduced medical errors in patient diagnosis and information transfer
HIPAA Compliance Checklist

Staying compliant with HIPAA can seem tedious at times but it is very important for all the covered entities and business associates dealing with PHI. HIPAA compliance requires a close understanding and implementation of the HIPAA Privacy Rule, Security Rule, and Breach Notification Rule as applicable to the entities. This is where a HIPAA Compliance Checklist will be of help.
Here is the 8-step HIPAA compliance checklist to help organizations get HIPAA compliant -
1. Understand the HIPAA Privacy and Security Rule
HIPAA Privacy and Security rules are both very closely related. Together they set rules for entities on protecting patients’ PHI and also instruct them about the safeguards to be put in order to protect this sensitive information.
HIPAA Privacy rule outlines the patient’s rights to protect their health records and other identifiable information. It also outlines how this data can be used or shared by entities only for authorized purposes.
HIPAA Security rule on the other hand dictates how the e-PHI of the patient can be created, received, used, or maintained by a covered entity. It also requires covered entities to implement Administrative, Physical, and Technical safeguards to ensure the confidentiality, integrity, and security of the e-PHI.
2. Determine if the Privacy Rule affects you or not
The Privacy rule primarily applies to all the covered entities (Health plans, health care clearinghouses, and health care providers dealing with PHI - according to the HHS), hence you need to be sure if your organization is a covered entity or not. Covered Entities under the HIPAA privacy rules are required to protect all forms of PHI, report HIPAA violations, and pay fines in case of non-compliance.
Though not directly stated but business associates also need to comply with the Privacy rule for their associated covered entities. Business associates need to keep in mind the patient’s rights concerning their PHI and how it should be used at all times. The covered entities must have a Business Associate Agreement (BAA) with all its partners and the rules regarding maintaining PHI security and overall HIPAA compliance by the BAs should be clear in this agreement.
3. Protect the right types of patient data
It is important to know what type of data needs to be protected under the HIPAA Privacy rule. HIPAA privacy rule enforces the protection of PHI which is defined as “Individually identifiable health information” of the patients.
Not all the information your organization collects is classified as PHI. It is important for organizations to identify what part of their collected data is actually PHI. Only this data needs to be extra protected using appropriate security measures and safeguards. Also only authorized individuals should be able to access this sensitive information.
4. Conduct a Security Risk Assessment
All covered entities should conduct an annual security risk assessment to understand the gaps in their security system. The Security Risk Assessment Tool by The office of the National Coordinator for Health Information Technology can be of great help for this assessment.
A periodic risk assessment helps monitor all the security measures implemented by the entity and find areas where the organization’s stored PHI can be at risk. It helps organizations understand if their security measures are compliant with the standards required under the HIPAA security rule.
5. Avoid potential HIPAA violations
HIPAA violations can occur in numerous ways, the most widely known of them are of course external hacks or data breaches, but surprisingly they are not the most common violations. In fact, the top 5 most common HIPAA violations that occur are the internal ones that can be easily prevented by organizations.
The top 5 HIPAA violations are -
- Accessing patient health records for unauthorized reasons
- Failure to perform a regular organizational risk assessment
- Lack of risk management process for the risks identified
- Failure to enter into a Business Associate Agreement with all partners
- Insufficient access control over ePHI
It is important to prevent these common HIPAA violations. Addressing all the security gaps, implementing technical safeguards such as encrypting data, using unique passwords, restricting access to PHI, and training all users about staying compliant, etc. helps avoid such violations.
6. Implement the Administrative, Physical, and Technical safeguards
Under the HIPAA Security rule, it is important for organizations to -
- Protect the PHI from any reasonably anticipated external threats
- Ensure only permissible use and disclosure of PHI takes place
- Training the workforce about being compliant
- Implement safeguards to ensure PHI security
HIPAA Security rule requires organizations to implement appropriate Administrative, Physical, and Technical safeguards in order to protect PHI data.
Administrative Safeguards
All the administrative actions involved in the development, deployment, and implementation of the ePHI security along with the management of the workforce dealing with ePHI are termed Administrative Safeguards. Examples of standard administrative safeguards are workforce security training, business associate agreements, conducting risk assessments, assigning a privacy official, PHI access policies, etc.
Physical Safeguards
The physical measures and procedures put in place to guard the organization's ePHI and its related buildings, infrastructure, and equipment against any unauthorized intrusion come under Physical Safeguards. A few examples of physical safeguards are security cameras, alarms, protection of portable devices (USB, Laptops, etc.), security plans for physical entry into record rooms, maintenance records, etc.
Technical Safeguards
The technology and the policy and procedures attached to handling such technologies for the protection of ePHI are termed Technical Safeguards. It is the most important of the three safeguards to ensure the protection of ePHI from external threats present. Examples of technical safeguards are encryption and decryption of data, data backup and storage, automatic logoff, access controls to ePHI, etc.
7. Detailed documentation of HIPAA compliance efforts
It is always better to document all the efforts made by the organization toward being HIPAA compliant. Constant documentation of all the essential HIPAA-related activities helps maintain transparency, address gaps in security, and mitigate risk.
This documentation can include OCR audit relevant documents such as policies and procedures, written and electronic communications, and actions requiring written records starting from the first draft to all the versions changed over time. All the documents holding PHI and detailed policies about disclosing and safeguarding PHI need to be kept for at least 6 years time. Also, documents such as audit logs, risk management process, BAA and other agreements, training records, list of vendors having access to PHI, etc. are relevant and valuable in case of a violation.
8. Report any breach of data immediately
In case of a data breach, it is the responsibility of the organization to have a plan of action. The organization must notify the OCR within 60 days of discovering the breach in cases when the breach affects more than 500 people. The organization also needs to inform the local media and all the people affected by the breach and open an internal investigation about the incident.
The OCR investigates all the breaches affecting 500 or more people and such breaches are listed on their Breach Notification portal as well. This 2-way investigation of breaches can help identify the reason for the breach faster and the security gaps within the organization can be fixed helping the organizations maintain their HIPAA compliance.
Final Thoughts
In conclusion, staying HIPAA compliant is critical for any organization dealing with PHI but it is not a one-time task. Achieving HIPAA compliance and maintaining it over time is equally important. It is an ongoing continuous effort for organizations to stay HIPAA compliant.
For all those who are looking to get HIPAA compliant for the first time, the above HIPAA compliance checklist will be of great help. While for organizations that are already compliant, following the checklist will help review their existing policies, safeguards, and documentation in order to stay HIPAA-compliant with the changing environment.
 SOC2 Type II
SOC2 Type II