9 Nerdy Ways to SSH into a Server

🔐 9 Nerdy Ways to SSH into a Server
In this blog we explore 9 fun and nerdy ways to make your SSH experience cool (and somewhat ridiculous).
🧙♂️ Use cowsay and fortune to Bless Your SSH
Install fortune
sudo apt update
sudo apt install fortune
For offensive or riddles
sudo apt install fortune-mod fortunes
Install cowsay
sudo apt install cowsay
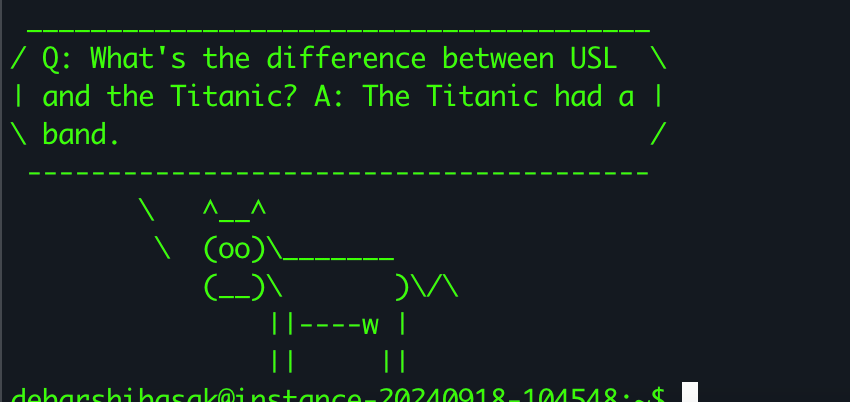
While SSH-ing into a server, run:
fortune | cowsay | ssh user@host
You should see
🖼️ ASCII Art Splash Screen
You can customize your login experience by adding ASCII art to your terminal every time you SSH into your server. Here's how to do it using figlet.
- Install
figlet
Debian/Ubuntu:
sudo apt update && sudo apt install figlet
- Generate ASCII art:
figlet "Welcome!"
- Edit the MOTD file:
sudo nano /etc/motd
- Paste the ASCII output, for example:

Save and exit. It’ll show up for all users at login.
🛰️ Run SSH Through a Satellite Relay (Using a Proxy)
You can use HTTP or SOCKS Proxy or SSH Relay or ProxyJump or sshuttle If the satellite network provides only proxy access:
In .ssh/config
Host remote
HostName remote-server
User user
ProxyJump user@satellite-relay
And then run,
ssh remote
🧙 Use sshpass with a Wand Gesture (or Smart Device)
Create a trigger script
Create an ssh script
#!/bin/bash
# wand_ssh.sh
sshpass -p 'YourPasswordHere' ssh user@hostname
Create a python script to trigger SSH.
import serial, subprocess
ser = serial.Serial('/dev/ttyUSB0', 9600)
while True:
line = ser.readline().decode().strip()
if line == "gesture:unlock":
subprocess.run(["/path/to/wand_ssh.sh"])
📟 Sound effects when doing SSH
For linux:
alias ssh='aplay ~/sounds/soundeffect.wav && command ssh'
Alternatively,
You can do Text-to-Speech.
For linux,
espeak "Establishing connection" && ssh user@host
For macos,
say "Establishing connection" && ssh user@host
🥷 Alias It with a Ridiculous Command
For eg.
alias initiate_protocol_x='afplay ~/modem.wav && ssh bbsuser@yourhost.com'
Then run:
initiate_protocol_x
🐍 Snake Game First, Then SSH
Install pythong
sudo apt install python3
Create snake_then_ssh.py
#!/usr/bin/env python3
import curses
from curses import KEY_RIGHT, KEY_LEFT, KEY_UP, KEY_DOWN
from random import randint
import subprocess
import sys
import os
def play_snake(stdscr):
curses.curs_set(0)
stdscr.nodelay(1)
stdscr.timeout(100)
sh, sw = stdscr.getmaxyx()
win = curses.newwin(sh, sw, 0, 0)
win.keypad(1)
snk_x = sw//4
snk_y = sh//2
snake = [[snk_y, snk_x], [snk_y, snk_x-1], [snk_y, snk_x-2]]
food = [randint(1, sh-2), randint(1, sw-2)]
win.addch(food[0], food[1], '🍎')
key = KEY_RIGHT
score = 0
while True:
next_key = win.getch()
key = key if next_key == -1 else next_key
head = [snake[0][0], snake[0][1]]
if key == KEY_DOWN:
head[0] += 1
if key == KEY_UP:
head[0] -= 1
if key == KEY_LEFT:
head[1] -= 1
if key == KEY_RIGHT:
head[1] += 1
snake.insert(0, head)
if head == food:
score += 1
food = None
while food is None:
nf = [randint(1, sh-2), randint(1, sw-2)]
food = nf if nf not in snake else None
win.addch(food[0], food[1], '🍎')
else:
tail = snake.pop()
win.addch(tail[0], tail[1], ' ')
if head in snake[1:] or head[0] in [0, sh] or head[1] in [0, sw]:
msg = " 💀 Game Over - Score: {} ".format(score)
win.addstr(sh//2, sw//2 - len(msg)//2, msg)
win.refresh()
curses.napms(2000)
return False
win.addch(head[0], head[1], '■')
def main():
result = curses.wrapper(play_snake)
subprocess.run(["ssh", "user@host.com"])
if __name__ == "__main__":
main()
Run it
chmod +x snake_then_ssh.py
./snake_then_ssh.py
🌐 QR Code Login
🛠️ Generate QR Code:
qrencode -o ssh-login.png 'ssh user@yourhost.com -p 2222'
Or plain terminal QR:
qrencode -t ANSIUTF8 'ssh user@yourhost.com -p 2222'
you can do
echo -e "\nScan to SSH into this system:"
qrencode -t ANSIUTF8 "ssh user@$(hostname -I | awk '{print $1}')"
Scan QR to Launch SSH on Desktop
sudo apt install zbar-tools
Script to Scan and Connect:
#!/bin/bash
zbarcam --raw | while read sshcmd; do
echo "Connecting with: $sshcmd"
eval "$sshcmd"
break
done
🎮 SSH via a Game Console Emulator
Running a guest OS inside a game console emulator allows for experimentation, development, and modding. This guide covers supported consoles and how to install Linux or other OS variants in an emulated environment.
🐧 Run Linux on GameCube/Wii with Dolphin Emulator + SSH (Optional)
Bring retro computing to life by running a guest Linux OS inside the Dolphin emulator, originally built for Nintendo GameCube/Wii. This guide walks you through booting Linux and optionally enabling SSH access from within the emulated environment.
🎮 What You’ll Do
- Boot a lightweight Linux OS on emulated Wii/GameCube hardware
- Access a terminal inside Dolphin
- Optionally enable SSH client or server for remote access or outbound connections
✅ Requirements
| Component | Description |
|---|---|
| 🐬 Dolphin Emulator | Download here |
| 🐧 Wii-Linux ISO/DOL | Linux build for Wii/GameCube (e.g., Mini Slackware) |
| 💾 Virtual SD card (optional) | To persist files or add SSH configs |
| 🎧 Modem sound (optional) | For BBS-style retro flavor |
🔧 Setup Steps
1. Install Dolphin Emulator
Download and install Dolphin from https://dolphin-emu.org.
2. Download Wii-Linux Image
Get a bootable .dol or .elf from:
Example:
wget https://example.com/wii-linux/boot.dol -O boot.dol
3. Launch the Image in Dolphin
Open Dolphin
Go to File > Open or Tools > Load DOL/ELF
Select your boot.dol
Dolphin should now boot into a lightweight Linux shell.
 SOC2 Type II
SOC2 Type II